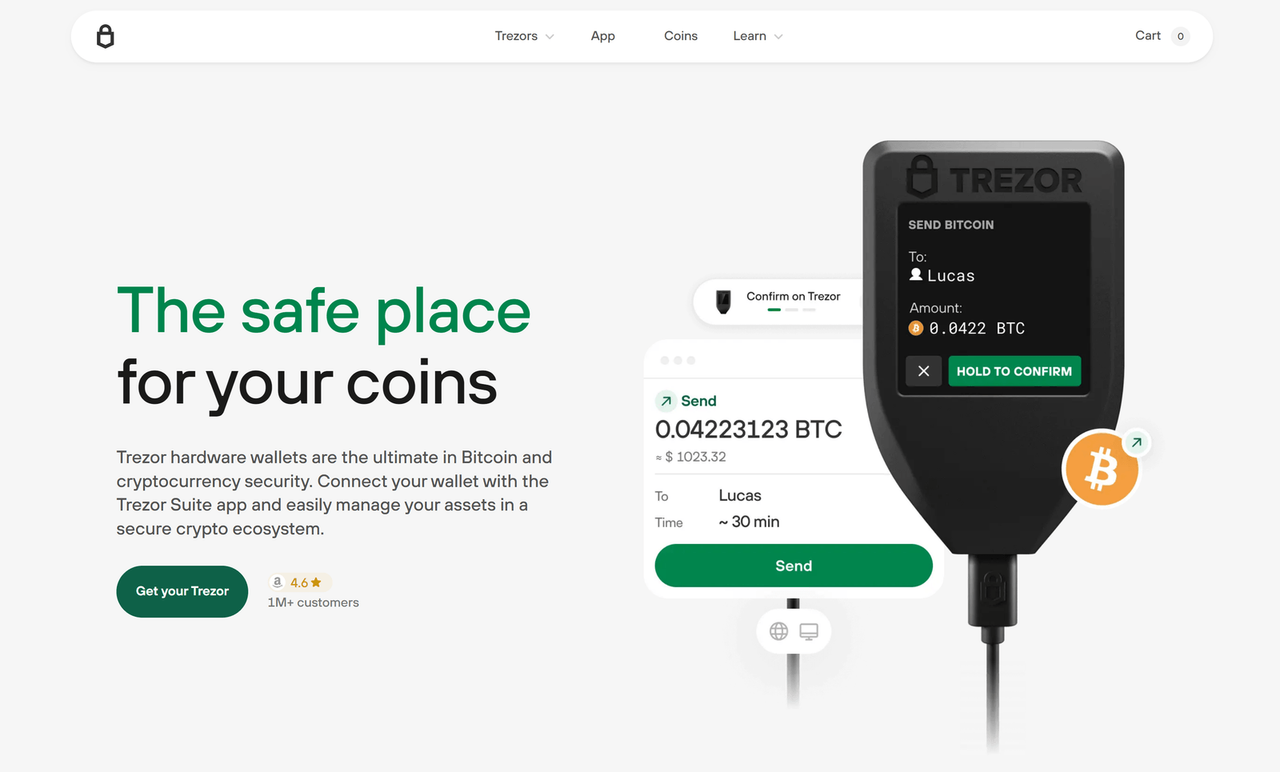
Understanding Trezor Login for Secure Cryptocurrency Access
Trezor Login is the authentication process that allows users to securely access their Trezor hardware wallet and manage their digital assets. With Trezor Login, users are assured that only they can authorize transactions, making it a vital security feature for safeguarding cryptocurrency holdings.
Why Trezor Login is Crucial for Digital Asset Security
Trezor Login provides a secure gateway between users and their cryptocurrency accounts, ensuring that private keys never leave the hardware device. By using Trezor Login, individuals can confidently protect their funds from phishing attacks, malware, and unauthorized access.
How Trezor Login Works Step by Step
Trezor Login functions through a secure communication protocol between the hardware wallet and a trusted interface, such as Trezor Suite. During Trezor Login, users confirm actions on the device itself, ensuring no sensitive data is exposed to their computer or the internet.
Setting Up Trezor Login for the First Time
To begin using Trezor Login, users first connect their Trezor device, install Trezor Suite, and create or restore their wallet. Once complete, Trezor Login enables secure access, allowing users to send, receive, and manage cryptocurrency safely from any compatible device.
Top 5 Benefits of Trezor Login
Trezor Login offers significant advantages for cryptocurrency users. Here are the top five benefits of Trezor Login:
- Maximum security: Trezor Login ensures private keys remain offline and out of reach from hackers.
- User-friendly interface: Trezor Login is designed to be intuitive, even for beginners.
- Phishing protection: Trezor Login helps verify legitimate websites and prevents unauthorized access.
- Multi-asset management: Trezor Login supports a wide range of cryptocurrencies in a single wallet.
- Cross-platform compatibility: Trezor Login works seamlessly across desktop, mobile, and browser interfaces.
Common Issues During Trezor Login and How to Solve Them
Users may occasionally encounter connectivity issues, outdated firmware, or browser conflicts during Trezor Login. The best approach is to update Trezor Suite, use trusted USB cables, and verify browser compatibility to ensure a smooth Trezor Login experience.
Advanced Security Tips for Trezor Login
To maximize security with Trezor Login, users should enable passphrase protection, regularly update their device firmware, and avoid using untrusted computers. By following these steps, Trezor Login remains a strong defense against digital threats.
The Role of Trezor Login in Decentralized Finance
Trezor Login plays an essential role in allowing users to interact securely with decentralized finance (DeFi) applications. By using Trezor Login, individuals can approve transactions directly on their hardware wallet, ensuring funds remain safe even when engaging with third-party dApps.
Final Thoughts on Trezor Login
Trezor Login is a critical component of cryptocurrency security, giving users confidence and control over their digital assets. Whether you are a new investor or an experienced trader, Trezor Login provides the robust protection needed to navigate the ever-evolving world of blockchain with peace of mind.
Made in Typedream